CyberMarket Update
Q3 2024
The cyber insurance marketplace was strong throughout the third quarter of 2024. Formidable competition existed between insurers to write new business. Cyber insurance premium decreases were the norm.
Insurers continue to be very interested in writing cyber policies. Capacity remains plentiful. Cyber MGAs continue to form and expand, which signifies the health of the market and the industry-wide desire to innovate in the cyber insurance space.
Cyber insurers were largely uninterested in expanding coverage in the third quarter. Ransomware and privacy claims outside the realm of data breaches continue to produce significant losses, so insurers were hesitant to change policy terms in ways that could increase losses. Insurers were willing to expand coverage on a case-by-case basis to win or retain business.
Insurers have taken steps to limit their exposure to certain types of claims. For example, in 2024 some insurers that have covered claims for the wrongful collection of data have put sublimits of $100,000 on that coverage. This is largely due to the growth of pixel litigation.2 Class actions are being filed against organizations using online tracking technologies such as the Meta pixel that track the movement of website visitors on the site in order to show them personalized ads. Those lawsuits have proved to be expensive to defend and resolve. Healthcare organizations have been hit particularly hard.
We did not see any changes to underwriting standards in the third quarter. Insurers continue to require organizations to have basic cybersecurity controls in place to qualify for broad cyber coverage. While standards haven’t changed, insurers are reacting to developments in the risk environment. One example is the questions being asked about the CrowdStrike outage.
The most forward-thinking insurers and MGAs are investing heavily in providing cyber risk management services. Those extend beyond free services and resources many other insurers offer and are similar to what an insured might receive from well-known third-party providers. Many of these services are of very high quality and quite reasonably priced for the value given.
The latest data from the Council of Insurance Agents & Brokers for the second quarter confirms the state of the marketplace.1 Unlike the first quarter, where the number of premium increases and decreases were equal, the second quarter saw nearly twice as many decreases as there were increases.
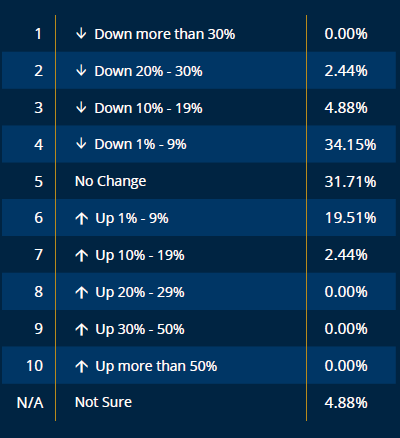
Source: CIAB Q2 2024 P/C Market Survey
After the ransomware attacks on Change Healthcare and CDK Global and their knock-on effects on thousands of customers in the first half of the year, everyone hoped the third quarter would be relatively quiet. However, that hope was dashed quickly.
On July 19, 2024, a defective software update to CrowdStrike’s Falcon Sensor product resulted in computers running Microsoft Windows failing to start up. The problem affected companies around the world. An early estimate of the resulting financial losses calculated them at $5.4 billion.3 Insured losses were estimated to be between $300 million and $1 billion.4
In addition to the losses it caused, the CrowdStrike event was significant because there was nothing Falcon users could have done to protect themselves from the defective update. Moreover, the resulting losses would not be covered under all cyber policies. A well-crafted policy with broad system failure coverage can respond, though. For cyber insurance purposes, system failure arises when a computer system becomes unusable because of events listed in the policy. Better policies expand coverage beyond the list in the policy.
The ransomware scourge persisted in the third quarter. According to the latest quarterly report from Coveware, a ransomware incident response firm, reported that the average ransom payment increased to $479,237, a 23% increase over the average for the second quarter.5 The median payment grew by 18% to $200,000. Phishing was the leading means of attack. Data theft took place in 76% of attacks. Healthcare, consumer services, and public sector organizations accounted for 44% of all attacks. Over 77% of attacks were directed against organizations with fewer than 1,000 employees. 37% affected organizations having 100 employees or less.
Data breaches, of course, continued in the third quarter. The good news is that the number is down from the first and second quarters.6
William Boeck
EVP, Cyber Product Leader
Tim Burke
EVP, Head of Cyber | Commercial E&O