TechnologyInsurance Pricing & Market Update
Q4 2022
Technology continues to be a primary factor for change in the world today.
Technological advances give businesses, governments and social-sector institutions more possibilities to elevate their productivity, invent and reinvent offerings and contribute to humanity’s well-being.1
The post-pandemic workplace continues to evolve and digital transformation has accelerated across every organization, which is forcing CIOs to keep up with pace.2 Additionally, IT departments must improve their maturity in key capabilities to maintain relevance in the organization3; and executive boards must give IT executives a seat at the proverbial table. According to Info-Tech Tech Trends 2022 survey, 79% of organizations will have a mix of workers in the office and at home.2 Hybrid work models have become a post-pandemic norm; CIOs have been at the forefront of hybrid work by facilitating collaboration between employees mixed between meeting at the office and virtually.2 To foster this collaboration, companies will continue to invest in tools adapted during the pandemic.2
Security strategies are essential for companies to control access to their digital assets and confidential data, providing access to only the right people and at the right time.2
Security strategies must adapt to a new caliber of threats in ransomware to avoid operational disruption and reputational harm.2 Therefore, organizations are being pushed to take a multi-faceted, Enterprise Risk Management approach to prepare for catastrophic losses.2
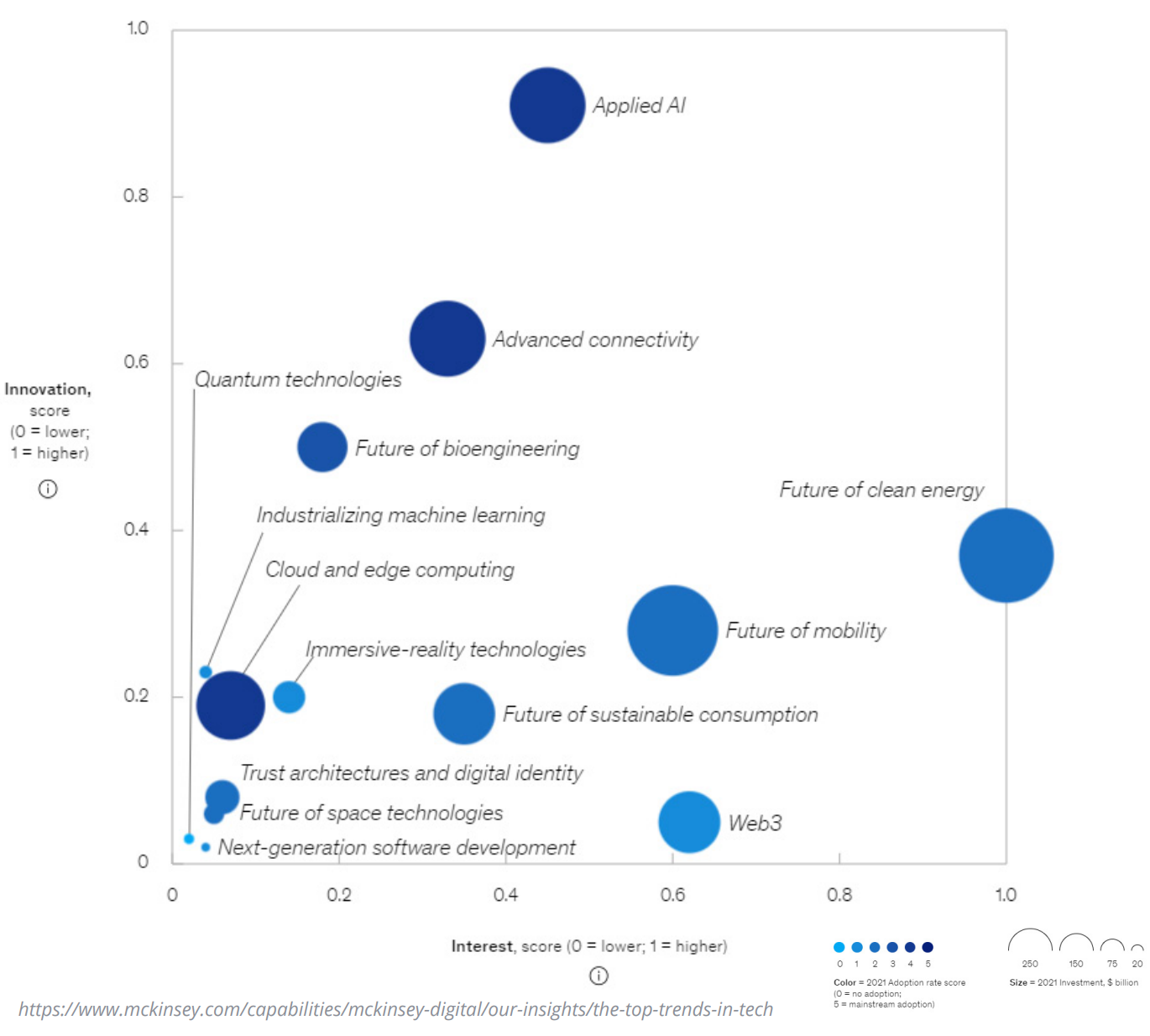
Technology is continuing to evolve at a brisk rate. The 2010s have been deemed the “Decade of Disruption.4 Within the past 10 years, Mobile networks have improved from 3G to 5G; the volume of data has increased from 2 ZB (zettabytes) to > 41 ZB; the pursuit of Genomics and Precision Medicines have driven the need for increased computing power, and Electronic Vehicles have changed the playing field in technology and advanced manufacturing.4
As the Broker of the Future, IMA aggressively tracks the technology trends and proactively employs education, risk management and bespoke insurance portfolios for our clients.
| Non-CAT exposed property with favorable loss history | 10% to 15% increases |
| CAT exposed property with favorable loss history | 25% to 40% increases |
| Property with unfavorable loss history and/or a lack of demonstrated commitment to risk improvement (unresolved recs, pattern of same issues, etc.) | 10%+ increases for non-CAT 30% to 50%+ increases for CAT exposed accounts and higher depending on frequency/severity of losses and when there are limited markets for a risk due to occupancy/class of business or concerns related to loss control |
| General Liability | Up 5% to 15% |
| Workers’ Compensation | Flat to Up 5% |
| Auto | Up 10% to 25% Up 30% if large fleet and/or poor loss history |
| Umbrella & Excess Liability – Middle Market | Up 10% to 25%+ |
| Umbrella & Excess Liability – Risk Management and other Complex/Hazardous Exposures | Up 25% to 150% |
| Professional Liability | Up 5% to 15%+ |
| Cyber | Up 20% to 30% |
Two companies that develop similar software’s which helps companies design and design their own applications went to trial over a trade secrets case. One company alleged that the other paid a government contractor to learn about their software, then handed the information over to a competitor.5 Around $2 billion of damages came about after the alleged stolen trade secrets helped the competitor lure away customers, some of which were top 5 tech companies in the world.5
On October 5, 2022, a jury found the Chief Security Officer at Uber guilty of criminal obstruction and concealment of a felony.6 Prosecutors alleged that this individual had failed to alert the FTC about a 2016 data breach at Uber which involved a hacker’s unauthorized access to customer records.6 The law firm commented that this “was believed to be the first time a U.S. company executive who had been criminally prosecuted over a cyber breach.”6
Users of TikTok who created videos on the app before Sept. 30, 2021, began receiving payments that followed a $92 million class-action data privacy settlement with the social media platform.7 TikTok was sued for violating Illinois’ strict biometric data laws by collecting and implementing facial recognition data into algorithms without user consent. Similarly, in May of 2022, 1.4 million current and former Illinois residents received checks and virtual payments from a similar $650 million lawsuit against Facebook, which allegedly used facial recognition data without consent to prompt users to tag their friends in photos.7
Pre-Claim: Take proactive steps to prevent a cyber breach or minimize its impact.
Disaster & Recovery Continuity: Maintain a detailed written plan that can be implemented with urgency on short notice.
Tabletop Exercises: Test the plan at least annually. Update and improve it based on the exercise.
Third-Party Vendor Selection: Identify third-party specialists to engage in the event of a breach. This includes an attorney, IT consultant, forensic accountant, public relations firm and ransomware negotiator. Vet these specialists and confirm a fee agreement if possible. Consider using the pre-vetted service suppliers suggested by your cyber insurance carrier.
Employee Training: Ensure staff members understand the technology systems they’re using. Reinforce bring-your-own-device policies. Require frequent training regarding phishing and “link bait” threats and consider using random simulations to test these vulnerabilities.
Multi-Factor Authentication: Require users to provide two or more verification factors to access IT resources.
Remote Desk Protocols: Create secure channels of access from staff home computers to the school’s IT desktop using VPNs and other safeguards.
Endpoint Security Protection: Integrate next-generation antivirus and behaviorbased protocols within the technology environment.
Offline Backups: Save data to a storage system unconnected to the school’s server frequently and regularly.
Invest in Quality Leaders: Ensure the school and school system are utilizing the highest level of internal or consultant IT expertise.
Post-Claim Best Practices: Adhere to the plan and avoid making the situation worse.
Communication Protocols: Notify your insurance carrier in accordance with your cyber policy terms and conditions. Notify other parties you’re obligated to inform per contractual agreements. Advise staff on a need-to-know basis, providing an appropriate level of detail in order to control external information releases.
Reporting to Authorities: Contact the appropriate authorities and regulators, not only in the event of a breach but in circumstances that could give rise to a breach.
Attorney-Client Privilege: Follow your attorney’s guidance regarding the release of any information to any party. 11
Assume Current Environment Remains Compromised: Adjust all electronic communication and IT activity as if the IT environment is still compromised. Maintain these practices until you receive assurance from reputable, third-party sources that the IT systems are safe.
Ransom Negotiation: Immediately engage with a third-party professional who specializes in IT ransom situations. Don’t negotiate without them.
Public Information: Control the information that goes public by ensuring all communication is released through your public affairs team or a third-party consultant. Confirm that is has been cleared by legal counsel.
Lessons Learned: Review what went well, what didn’t go well and what was missed. Revisit and improve your IT environment and your Disaster Recovery & Continuity plan based on this experience.
Alex Fullerton
Marketing Specialist
Renee Stock
VP, Senior Advisor and Consultant:
Advanced Industries Specialty