An article from the Wall Street Journal identified cyber-security threats and intense competition for talent as two of CEO’s top concerns for 2018. Our IMA experts, Tim Burke and Jessi Ryan, weigh in on how to succeed in these areas:
In Other News
- US adds 148,000 jobs in December, but misses analyst expectations
- Intel hardware security flaw affects iPhones, iPads & Macs
- President of Philadelphia Fed indicates two rate hikes in 2018
- Tesla misses production estimates
- Travis Kalanick unloads 1/3 of his Uber stake
The War for Talent
In today’s war for talent, it is the job seeker’s market and employers need to think strategically just to keep up. With the jobless rate at a 16-year low and a record 6 million open jobs, employers are struggling to find the talent they need to fill those roles as many job seekers may not have the required skill set. At the same time, internally, employers are being tasked with answering their employees’ desire for personal and professional growth opportunities.
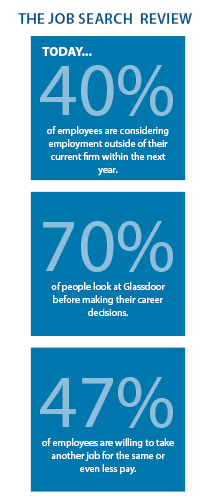
Employers find themselves in fierce competition fighting for top talent, and must strike a balance between the need to retain the great people they currently have while also attracting new talent that is compatible with their organizations. With 70% of job seekers using tools such as Glassdoor to evaluate whether they want to work for a company (based on employee reviews) and over 40% of employees currently seeking employment outside of their current firm, it’s crucial for employers focus on creating a top-notch employee experience.
To do so, some employers may choose to focus on training and development. By implementing strong training and development programs, employers can attract employees that may not have the current skill set required for a role, but can hire based on cultural fit which could prove to be even more beneficial in the long run. Some employers pause at this concept because of the risk of investing in training an employee that ultimately may leave to work for a competitor. In this case, our team likes to quote Richard Branson: “train people well enough so that they can leave, treat them well enough so that they don’t want to.”
Ultimately employers need a strong focus on creating an excellent employee experience to remain competitive. At IMA, we work with clients to understand what their people specifically value as a part of their work experience; we collect data points from across the company and use analytics to help employers optimize the dollars invested in their people. Our unique process and insights enables our clients to craft a unique employee value proposition that will help recruit and retain top talent.
Cyber Threats
Board members and executive management across varying industry groups consistently cite managing cyber threats as a top area of concern. The primary concern is how events might disrupt core operations, that 64% of HR professionals believe data security and cyber risk will become challenging in 2018 is symptomatic of the expansion of awareness, not just in the C-suite, but throughout organizations
The first step in addressing Cyber Disruption is to acknowledge that it an enterprise risk and treat it accordingly. That will start with leadership fostering a culture of vigilance and accountability. This is not an “IT problem” and everyone in the organization needs to actively manage the risk. While one size does not fit all, we regularly counsel and assist our clients to take some basic first steps.
- Awareness: Create a separate and distinct budget for IT security. Engage a qualified third party to provide an annual security assessment. You cannot audit yourself and it is essential to have an objective review of your operations. Include within the budget funds for the remediation of high level risks and maintain a roadmap of remediation efforts.
- Mitigation: Train your employees! Our experience has been most Cyber losses occur due to employee failure. Examples include social engineering exploits and theft of credentials. Employees must understand what to look for and how to respond.
- Response: The greatest variable in resulting financial loss and reputational damage is how an enterprise responds to a Cyber event. Recent history is full of examples of how not respond (EX. Equifax) and the prolonged damage. Due to the size and complexity of potential Cyber risks, every organization will witness some form of event. Each organization should have some form of a Cyber incident response plan. The plan should be maintained and implemented by the core leadership team. Most events will require utilization of third party experts such as legal counsel, forensic investigators and public relations. Those service providers should be identified within the plan. The plan should be regularly tested to include real world simulations.
- Risk Treatment: To effectively manage Cyber risk an organization must identify and quantify material risk factors. Key stakeholders should assemble to agree on the top ten to twenty risks and assign values of probability and severity. Emphasis should be placed on unique operational and industry attributes. Once this list has been assembled there should be an analysis of the current insurance portfolio to determine if risks are insured. Since traditional Property & Casualty policies were not designed to address Cyber risks (and often exclude), it is now commonplace to look to stand – alone Cyber insurance policies to transfer high value risks off the balance sheet. Cyber insurance carriers provide a wide variety of loss control and can provide resources to accomplish steps 1-3 above.